Website Deployment & Server Management, made simple!

All-in-one platform
ServerAuth offers a comprehensive, all-in-one platform for seamless server and site management.
Streamline your operations, simplify workflows, and efficiently handle all aspects of your infrastructure from one centralized solution.
Server Management for Web Agencies Server Management for Freelancers Website Management Start A Free TrialSelect a custom server, or provision automatically with DigitalOcean, Hetzner Cloud, Akamai or Vultr.
Specify your site type, PHP version and additional options such as database credentials and cron jobs.
Once you're ready to go live, or to our included staging environment simply click deploy.
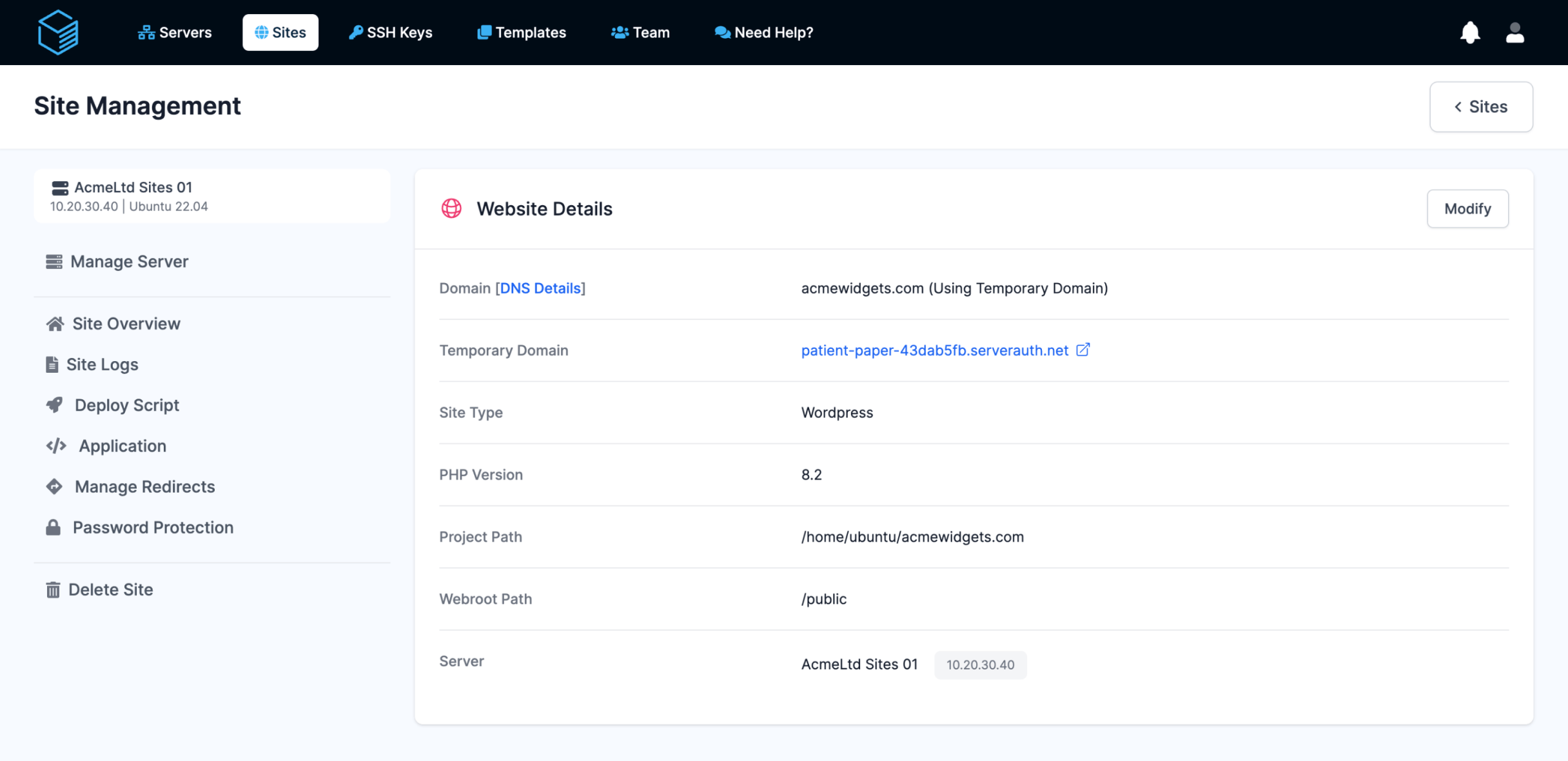
1-Step Wordpress Deployment
Simplify deployment of sites with our built in WordPress website deployment and management tools, with support for using our free temporary domains during development, options to configure your cron jobs to improve WordPress performance and more.
After providing your site details your shiny new WordPress site will be available within seconds!
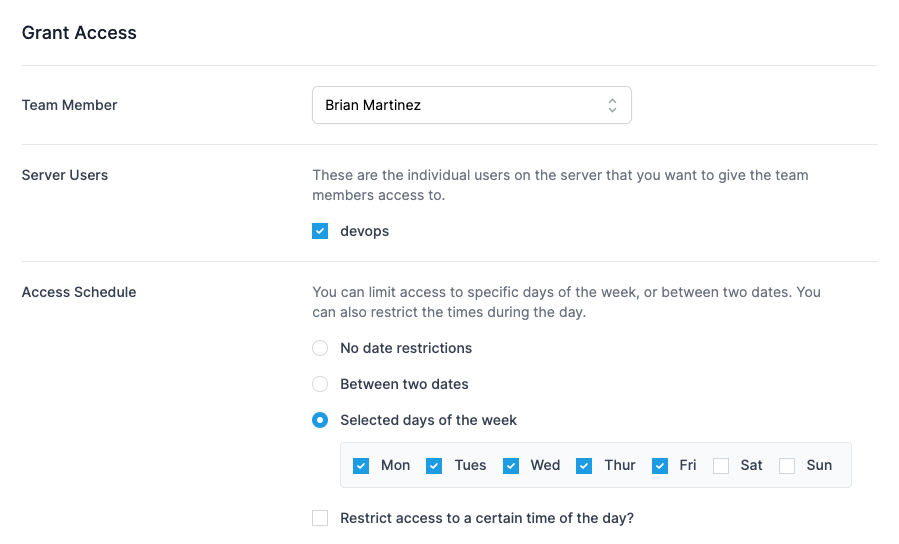
Control who can access your servers, and when
With Scheduled SSH Access controls you can choose when your team, contractors and clients can access your servers via SSH.
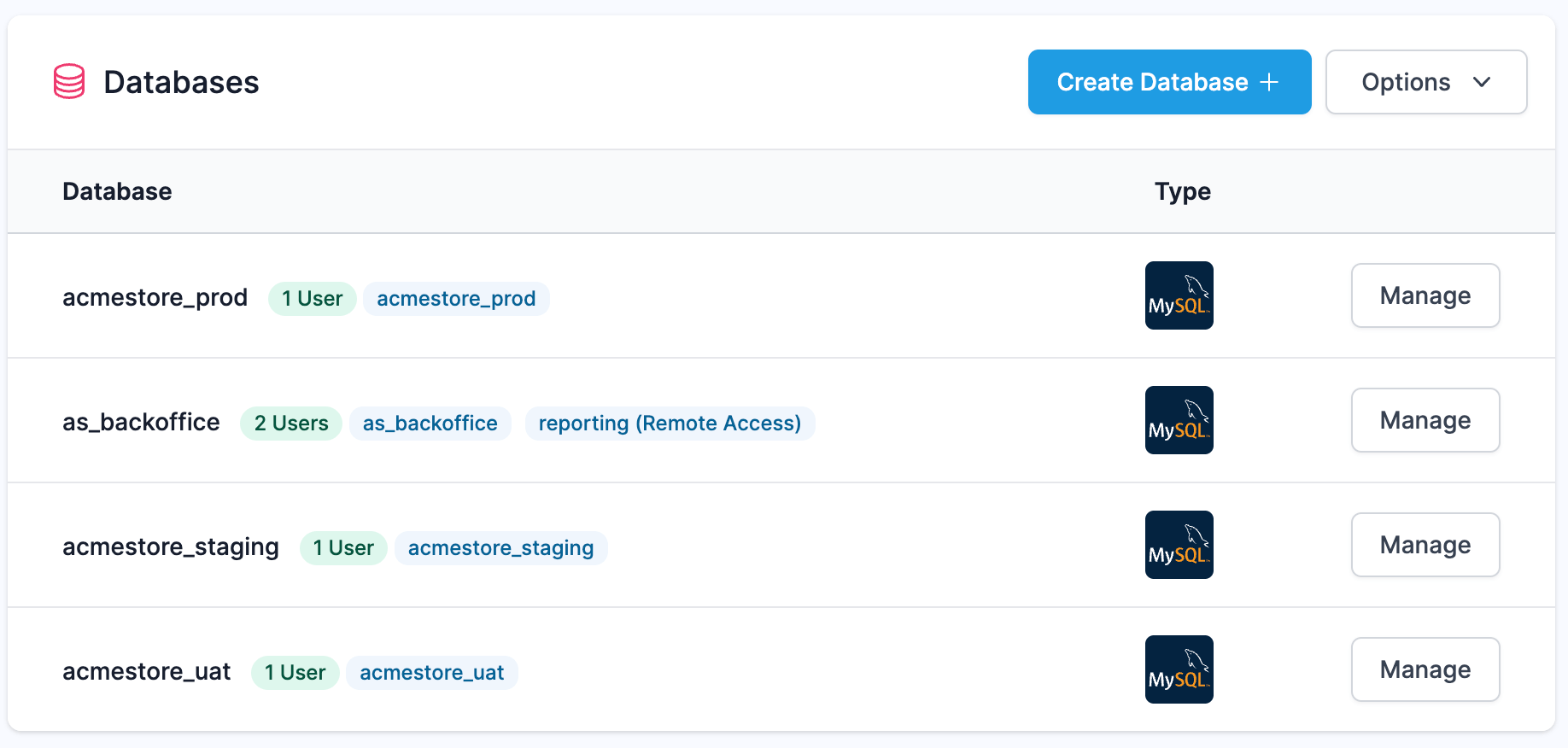
Manage your MySQL Server
Our MySQL database management feature allows for easy 1-click-installation and management of MySQL on Linux-based servers. Create and manage databases and users all from the convenience of our web interface.
In addition to managing databases and users, our database management feature also allows you to manage remote MySQL user access.
We provide a range of pricing plans for different sized organisations. Depending on which plan you may have different limitations on the number of servers and/or team members.
Check out our pricing page to find the plan that best suits your needs.
Yes, We only store your public keys. Public keys alone can not provide someone with access to your servers. We've written more about it and provided links to other sources, in our help docs.
Our advanced integration, which provides server management features, supports the latest and LTS versions of Ubuntu (20+) and Debian (11+).
Our legacy integration, which provides just SSH access management and server monitoring supports Ubuntu 18+, Debian 9+, CentOS 6+ and Fedora 10+.
If you are using a variant of one of the above supported operating systems (e.g Rocky Linux, Alma Linux) then you'll likely still be able to use ServerAuth. Please get in touch if you are unsure, or if you use another operating system that you would like us to support.
Our basic integration, which provides SSH access management and server monitoring uses a server-site agent, meaning we do not need to know any details about your server, or have any access.
To make use of our Advanced Integration, which gives you access to our server management suite, our isolated backend will have access to perform selected actions. This will be done from a secure system, which is not accessible outside of a private network, nor is it accessible to ServerAuth staff. At no point do our staff have the ability to directly access your servers.
Unlike other server management systems our client-focused control panel does not directly communicate with your server.
Check our our security page for details on the steps we take to ensure we can provide a secure and risk free service.

